Gmail Users Beware: Even Developers Are Falling for This Scam


Read in other languages:
The popularity of Gmail and its integration with a growing number of apps and websites has become a goldmine for hackers. As new safeguards are continually added to the system, attacks are also becoming increasingly sophisticated. A new phishing scheme designed to steal sensitive information is now targeting Gmail users, and even developers have been fooled by it. Here's how to spot the threat and protect yourself.
It is not unusual for Google to issue warnings about rising threats, including new types of scams and phishing tactics. This latest case follows a similar pattern, using weaponized websites that are increasingly difficult to detect.
- Also read: Android users shall never install this app
Gmail Phishing Disguised as a Voicemail Alert
According to a report published by malwr-analysis, Gmail users are being targeted by a new phishing attack. The scheme begins with an email labeled “New Voice Notification,” sent from a spoofed sender. Notably, the phishing campaign uses Microsoft’s Dynamics platform to bypass email filters and anti-spam protections.
Inside the email, there is a button prompting users to open the voicemail on a separate website. This site features a fake CAPTCHA security prompt that victims must complete to proceed. The CAPTCHA is part of a broader mechanism designed to make the page appear legitimate and earn the user’s trust.
Once the CAPTCHA is completed, the victim is redirected to a cloned Gmail login page where they are prompted to enter their account credentials. The interface closely resembles the authentic Gmail login, making it extremely difficult to distinguish from the real one.
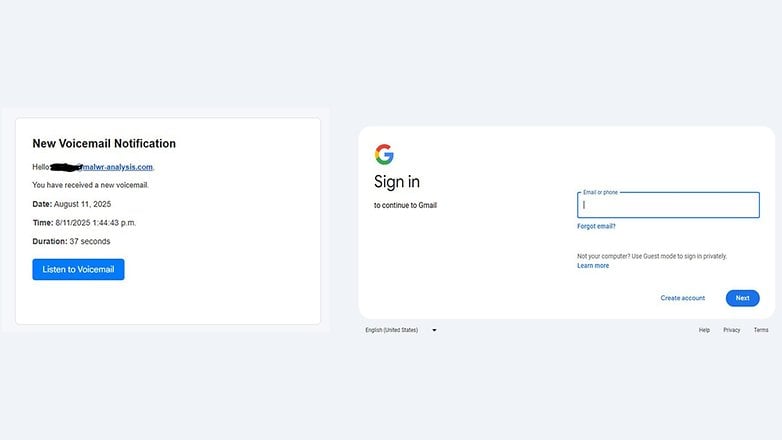
What is especially alarming is how the page’s script uses AES encryption to hide its identity and incorporates anti-debugging techniques, making it difficult even for developers to recognize it as a fake website.
On this page, any sensitive information entered by the user is captured by the attackers. Beyond just usernames and passwords, the system is also designed to collect additional credentials such as backup email addresses, two-factor authentication codes, and answers to security questions.
The stolen information is then transmitted to attacker-controlled servers, where it can be used to access your Google account and any connected services.
How to Protect Your Gmail and Passwords from Phishing Attacks
Users can protect themselves by carefully inspecting voicemail alerts and similar messages received in their Gmail inbox. At the same time, regularly updating your Google password and choosing stronger credentials is strongly recommended.
Additionally, transitioning to passkeys is encouraged. Passkeys are a newer and more secure authentication method that rely on biometric verification, such as facial recognition, fingerprint scanning, or PIN combinations, instead of manually entering usernames and passwords.
Are you already using passkeys on your devices? What other steps do you take to enhance your security and safeguard your personal information? Share your thoughts in the comments.
Via: Cybersecuritynews Source: Malwr-analysis