How to use locked apps on a rooted phone

SafetyNet is the word on everyone's lips. This defense measure from Google rose from the idea that app developers could protect their services against fraud. This is because it's theoretically possible for app data to be manipulated when a phone is rooted. Nevertheless, SafetyNet is also often used without obvious reason. Those who mod apps as a hobby and various developer communities view SafetyNet as an enemy. Here you'll discover which apps use SafetyNet, and and how to use apps like Pokémon GO or Snapchat on a rooted phone.
The situation has escalated since my first article on the topic of SafetyNet. While the list of apps protected by SafetyNet hasn't changed, the mechanism by which SafetyNet works has intensified. In addition, Google has removed the secure root tool Magisk Manager from the Play Store. Even the community behind Lineage OS has announced that it will no longer be able to circumvent SafetyNet's checks.

Which apps lock themselves via SafetyNet, and how?
Unfortunately, there isn't a complete list of SafetyNet-protected apps, but we can share a few known examples. These utilize SafetyNet's checks in different ways. Some can also be bypassed, while others are permanent.
Netflix, for example, is invisible in the Play Store if your device doesn't comply with SafetyNet checks. You can however, download Netflix from external sources like APKMirror using a rooted smartphone. You could then install it, register (even with Google Smart Lock) and use the service without restriction. But the app won't automatically update via the Play Store. For that, you'd need to use an alternative app store.
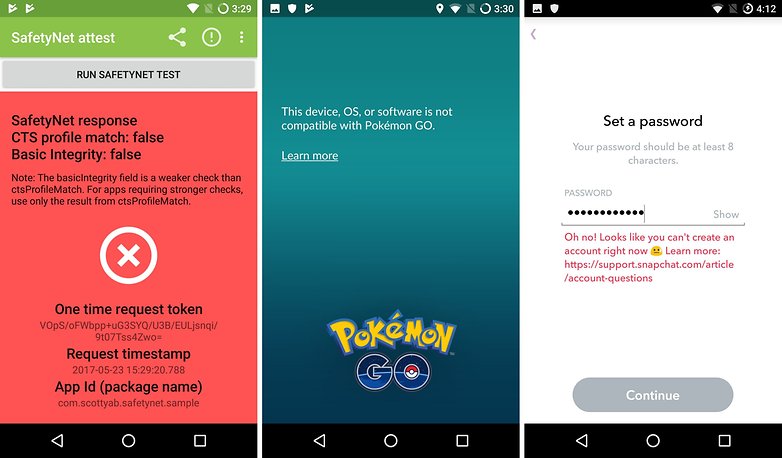
Snapchat will check your SafetyNet status only during your first login. If you root your smartphone after installing Snapchat, you can continue using the app as normal. But this doesn't work the other way round, as Snapchat will no longer allow you to login after rooting.
This is similar to Pokémon GO. But with this app, your SafetyNet status is reviewed with every launch. If this fails, an error message will appear saying registration isn't possible. As the SafetyNet guidelines can change from day to day, this game of cat-and-mouse between Google and apps bypassing SafetyNet can almost be followed live.
Super Mario Run is even stricter still. If the SafetyNet requirements are not met here, the app will simply crash without comment. Nintendo also appears to search for Magisk's app-ID. This runner game will only start once Magisk as well as Magisk Hide are activated.
In the land of Android Pay, SafetyNet is a sharp sword for all users of the payment service. Because of SafetyNet's restrictions, it's often impossible to use your phone as a reliable mode of payment, even with apps like Magisk. Like Netflix, Android Pay will notice even an unlocked bootloader.
Bypassing SafetyNet with Magisk
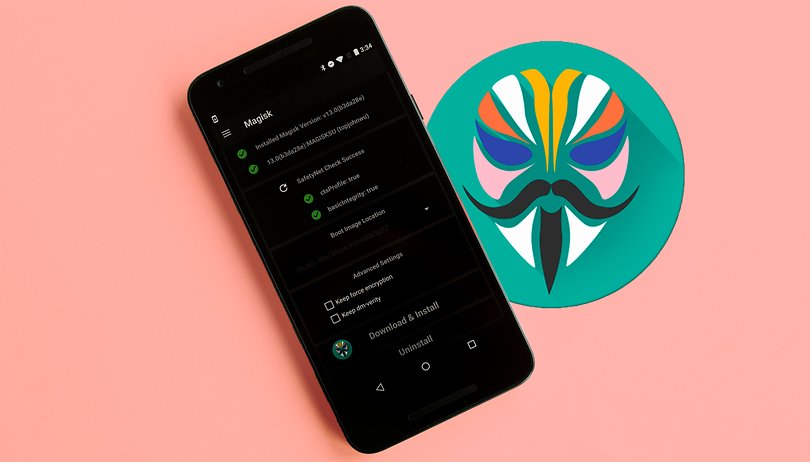
The short-term solution to circumvent SafetyNet restrictions is with root hiders like Magisk. This tool is an all-round package, because you can also use it to manage root access. SuperSU or Chainfire's CF-Auto-Root are thus no longer necessary.
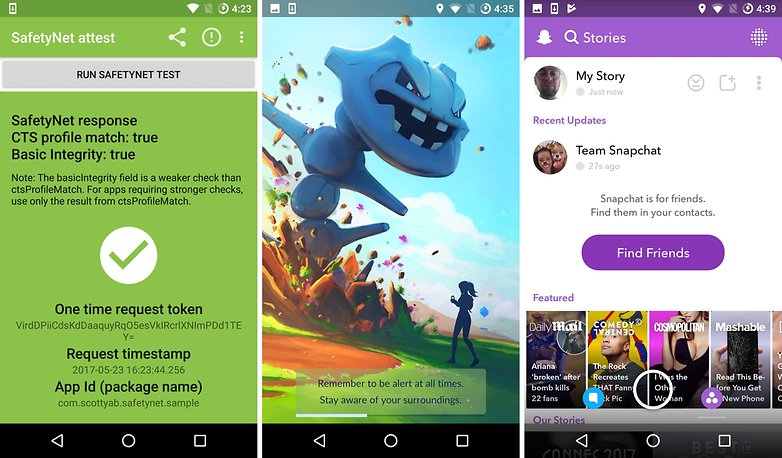
Until recently, the Magisk Manager was still available in the Play Store. With the provision of custom recovery, it could easily root your device and also return it to its SafetyNet-compliant form. As of right now, there is only one ZIP file of a current Magisk beta available for download. This bypasses SafetyNet updates from (presumably) June 13, 2017. But this update may already be obsolete by the time you read this article. After all, the Magisk Manager can update itself.
Magisk provides additional options to evade the SafetyNet check. The app can hide itself and other installed apps, switching to a minimal "core-only" mode. That said, it cannot perform miracles.
SuperSU creator Chainfire has already said last summer that the current methods for disguising root modifications have no future. He elaborates: "as long as the number of people using these tricks reaches a critical mass, smartphone manufacturers will provide patches against these methods."
Magisk project manager Topjohnwu claims that because of their root privileges, these tricks from Magisk will always outmaneuver root-free SafetyNet control methods. But like Chainfire, he also concedes that smartphone manufacturers establish devious control mechanisms through the use of protected file systems. Modders will find these more difficult to understand. He speaks directly of Google Pixel, whereas Chainfire mentions Samsung.
It's not just about the root
The SafetyNet API was designed primarily to detect infected or incompatible devices. What the developers behind Magisk or other root hiders do to evade checks is largely similar to malicious malware, and this is beyond doubt.

App developers don't need to use SafetyNet in their apps. But there are nevertheless understandable reasons why they'd want to make use of this offering from Google. Apps like Spotify or Netflix fear that these root privileges may extract your downloaded offline content from the data system, crack the copy protection and then offer your data for download. Online banking apps or Android Pay may worry that financial transfers could be observed or performed by unauthorized third parties.
With lifestyle apps however, this reasoning seems tenuous. Snapchat may be in trouble, Super Mario Run and Pokémon GO may guard against cheating. But do they need to use such heavy defense methods like SafetyNet? I would bet that Magisk is primarily used for one or more of these three apps.
SafetyNet doesn't just look at the root, it can be even more rigorous. Even unlocked bootloaders or software which is different from the original firmware will be detected and registered. The app developer will then decide how to deal with this response. In the case of Netflix, the app is invisible in the Play Store for every custom ROM, even if you haven't rooted your device. Denying root access was normal, even in the younger editions of custom ROMs, to guard against SafetyNet reprisals.
What's it all about then?
The current, indiscriminate use of SafetyNet raises a lot of questions. Some banking apps don't use SafetyNet, although they perhaps should. Instead, a detected root access will trigger a warning, but then the app continues to run smoothly. After being sideloaded, Netflix can be used without restrictions. I could find and copy downloaded episodes in the file system (with DRM).
And top of this comes all of the non-critical apps like Snapchat, including games such as Pokémon GO and Super Mario Run whose use of SafetyNet will possibly deter cheating. But aren't we using a sledgehammer to crack a nut here? And do tools like Magisk have a right to exist?
On the other hand, I also ask myself if there's still any justification for rooting at all. Thanks to Google's backup function, which now works reasonably well, reasons for rooting such as Titanium Backup are not as compelling as they once were. Of course, I'm happy about theoretically having more control over my smartphone, but the restrictions of an unrooted smartphone aren't exactly intolerable.
What I understand least is the punishment for unlocked bootloaders. If I want to equip an old smartphone with a custom ROM like Lineage OS, I'm doing this in the interest of security. By using newer patches which are banned by the manufacturer, I'm actually making my device safer than using the manufacturer's firmware. For this, I'd be unjustly punishe, and I find that alarming.


















Oh, yes, Android backup "works reasonably well". Only if that means it'll backup about 1/5th of your apps and data and developers are free to turn on a no-backup flag for no logical reason at all. So, getting a new phone or an insurance replacement is a Herculean chore that I would much rather not spend my time on.
It's great to get a new phone but then having to spend 12 hours downloading all of my apps again, losing the majority of my data, and praying that every single developer enabled a 3rd party cloud backup or the childishly simple task of enabling backup to Google Drive within their code.
I'll give you a hint the latter is about 1 in 100.
Even the Samsung Smart Switch backup is abysmally bad.
FFS, Google, remove the no backup flag and the number of devices that will be end up being rooted will probably be easily cut in half.
As much as I hate to compare Android to iOS, iOS blows Android out of the water and out to Mars when it comes to data backup, unfortunately iOS sucks at everything else, including freedom of the user to otherwise do what they want.