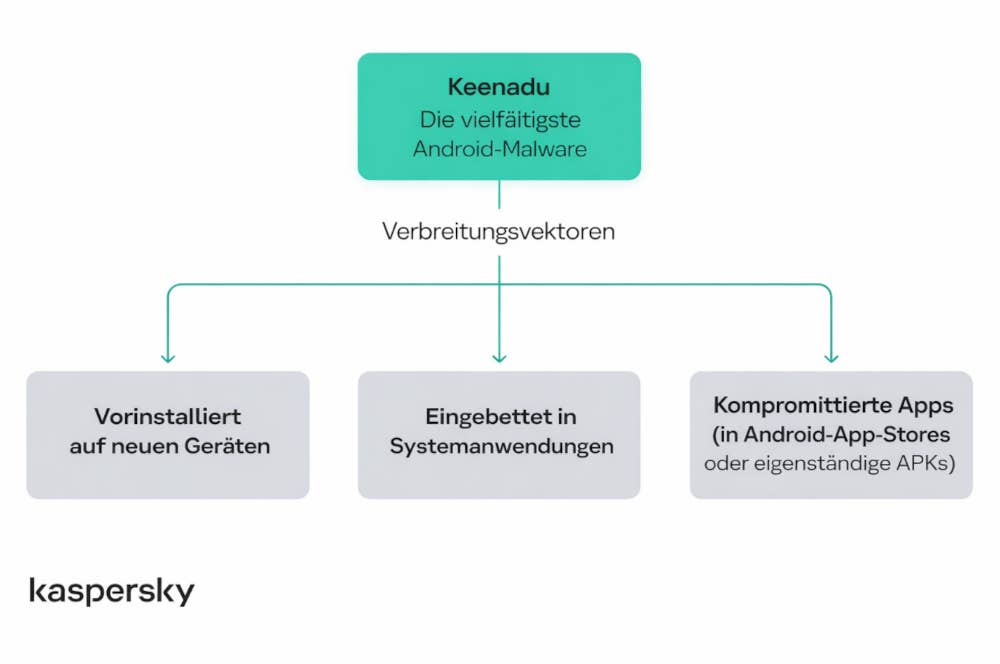
An analysis by Kaspersky reveals how Keenadu spreads through various channels. First, the malware has already been found in the firmware of certain Android tablets. This means devices may already be infected when they are unboxed. Second, Keenadu appeared in pre-installed system apps. The security firm also found infected applications in app stores, including the Google Play Store.
Keenadu Malware Relies on Three Distribution Channels
Keenadu is currently mainly used for advertising fraud. Infected apps open invisible browser tabs in the background to call up websites and generate advertising revenue. However, some variants go further: they enable attackers to gain complete control of the infected device.
The firmware variant is considered to be particularly dangerous. Similar to the Triada backdoor that was discovered in 2025, Keenadu can deeply embed itself within the system. In this form, the malware acts as a full-fledged backdoor. It can manipulate apps, install additional applications, and grant far-reaching authorizations.
This way, messages, photos, location data, or even banking access data could be tapped, among other things. Even search queries in Chrome’s incognito mode can be monitored under certain circumstances. Interestingly, the malware does not activate if the device is set to a Chinese dialect and uses a Chinese time zone.
Malware in System Apps and Smart Home Applications
Kaspersky also found Keenadu in system apps, such as a facial recognition app. There is a theoretical risk that sensitive biometric data could be accessed this way. The malware was also partially integrated into launcher apps. Infected apps for smart home cameras recorded particularly high downloads on the Play Store. There were more than 300,000 installations before they were removed.
What Users Should Do Now
Kaspersky advises users to use a reliable security solution to be protected against malware like this. Users should also check whether firmware updates are available and perform a full scan of their smartphone or tablet as a precaution. Compromised system apps should, if possible, be uninstalled and no longer used.
The Keenadu case shows how Android malware is becoming increasingly sophisticated once again. It can even sneak deep into the supply chain where no smartphone or tablet buyer expects it. If you want to stay safe, check your devices regularly and install available updates promptly.






