In recent months, numerous cyber threats and attacks have intensified, driven by increasingly sophisticated tactics. While warnings had already been published before, the U.S. top security agency is now sounding the alarm, cautioning millions of users of popular messaging apps like WhatsApp, Telegram, and Signal.
The alert was issued by the Cybersecurity and Infrastructure Security Agency (CISA) on Monday. It addresses users of established communication platforms, warning that malicious actors are using “sophisticated targeting and social engineering techniques” to compromise individuals.
How Attackers Use Messaging Apps to Target Victims
One of the techniques highlighted by the agency is zero-day exploits that require no interaction from a user. This has proven to be one of the most effective forms of attack, though it often relies on a loophole in the device. Additionally, attackers use QR codes that trick users into scanning malicious links or websites, as well as fake versions of messaging apps designed to hijack mobile devices.
The report also cites examples of these attacks, including CVE or Common Vulnerabilities and Exposures, which track flaws and exploits in mobile devices. Cases include the spyware campaign ClayRat that targets Telegram users and Landfall spyware impacting Samsung Galaxy devices in the Middle East.
Once infiltration is successful, attackers can deploy additional harmful payloads to gain deeper access and compromise both the phone and the victim’s accounts. For instance, spyware can be planted to extract sensitive information.
CISA noted that while these threats affect general users of messaging apps, high-profile individuals in sensitive environments such as government, politics, and the military are more frequently targeted. The agency also reported that these attacks have been observed in regions including the U.S., Europe, and the Middle East.
Users Should Enable These Features to Stay Protected
While not everyone needs to panic, general users are advised to adopt basic safeguards. The most important step is keeping phones and apps updated to the latest software. In addition, avoid clicking suspicious links and refrain from installing apps from unknown developers or unverified sources.
Messaging app users should ensure their service offers end-to-end encryption. They should also use a password manager to store credentials and avoid weak authentication methods such as SMS. Instead, migrating to passkeys is recommended.
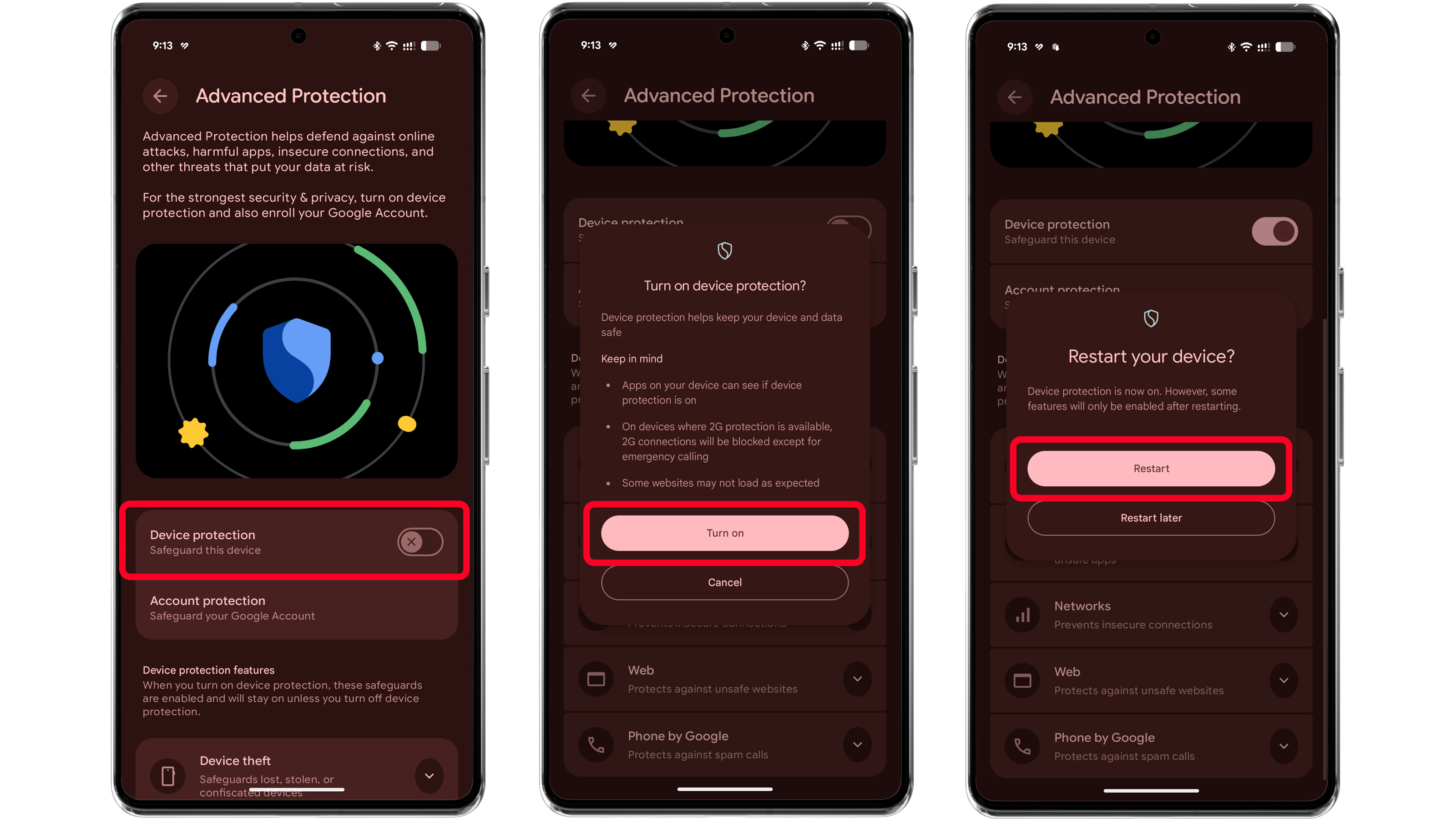
During an attack, users can enable on-device security features. On iOS, Lockdown Mode provides extra protection while limiting certain functions. Android offers a similar feature called Advanced Device Protection, which enables safe browsing, disables trackers, and blocks unsafe networks.
Do you follow any of these security and privacy measures when using your device or going online? We would like to hear your experience.




