Security Briefing: All the Information We Know About the USSD Exploit



Yesterday, an Android security problem was discovered which has turned out to be more serious than we had originally thought. Not only Samsung but a number of other Android smartphone manufacturers are affected. Here, we give you an overview of the situation.
Patient 0:
On the 21st of September, the Indian developer Ravi Borgaonkar held a security conference in Buenos Airies, titled "the Abuse of USSD codes on mobile networks." To demonstrate the serious security problems associated with USSD codes, he wiped a Galaxy S2, simply by clicking on a link on a malicious website.
Link to Video
How did it happen?
Borgaonkar entered the USSD code *2767*3855# on his Galaxy S2, which reset his phone to its factory settings; a process which is performed differently on different Android models. On some, like the HTC One X, the device asks you whether or not you want to delete all your apps and restore your phone to its factory settings or if you want to do that AND delete all your pictures, music, and personal files saved to the SD card. On the Galaxy S3, the process (just) deletes all your apps, system application data and settings.
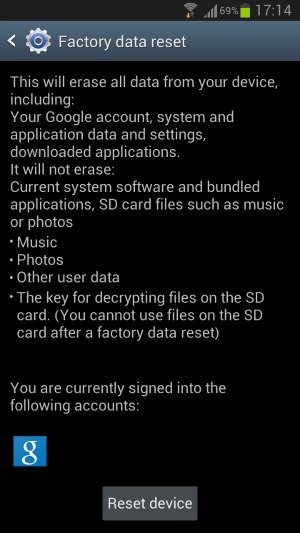
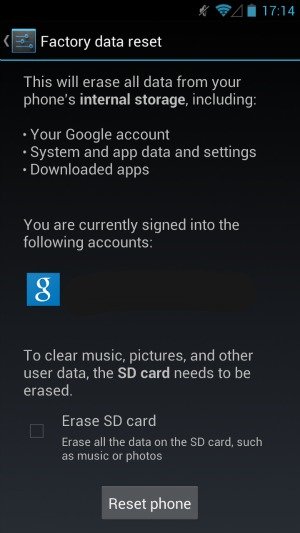
The factory reset page on the Galaxy S3 (left) and HTC One X (right). Notice the HTC One X offers users the ability to also erase the SD card.
What is a USSD Code Anyway?
A USSD code is entered into phones to perform actions. They are mainly used by network operators to provide customers with easy access to pre-configured services, including call-forwarding, balance inquiries and multiple SIM functions. These shortcuts are also used by many manufacturers to control system functions. But they are mainly intended for internal use and thus rarely communicated to the user.
Where is the Security Hole?
Normally, when entering a USSD code, you must enter it into the keypad of your phone and tap the call button. But Borgaonkar's code skips this step and automatically runs in the background, without the user noticing anything.
The USSD code links the browser to the phone app. That means: When I click on a telephone number in my browser, the phone App opens with the previously clicked number and I only have to hit the "call" button.
The HTML code to execute such an action is as follows:
<a href="tel:xyz">Click here to call us directly</a>
Now, I only need to replace the "xyz" with the USSD code *2767*3855#, and the HTML code becomes far more nefarious:
<a href="tel:*2767*3855#"> Click here to call us directly </ a>
The command above assumes that the user clicks on the link, so that the phone app is launched. Borgaonkar has embedded this command in a frame, which looks like this:
<frameset> <frame src="tel:*2767*3855#" /> </ frameset>
Now, if this code is embedded in a website and the smartphone visits the site, the phone will immediately and without further inquiry dial this number. But that in itself is still not the problem, since usually the user would have to explicity tap the call button in order to dial the number.
But the security breach is worse than that, since the call is immediately performed in the background, without any confirmation needed by the user. Rather, the call is placed covertly. And if hiding behind the number is not a phone number but a corresponding USSD shortcut, there is a problem. In Borgaonkar's demonstration this means that the Galaxy S2 can visit a malicious website and immediately begin the factory reset without the user knowing what's happening.
So this is not just a Samsung issue but an Android issue, as well?
Yes. Running USSD codes in the background via a malicious website seems to be a cross-vendor problem. Samsung only had the misfortune of being the test dummy. Already, folks have demonstrated the issue on Motorola and HTC phones as well.
Are there any other entry points?
Yes, any app that has access to your browser can perform this action automatically via a website. It can perform the action via QR codes, NFC tags and WAP Push messages.
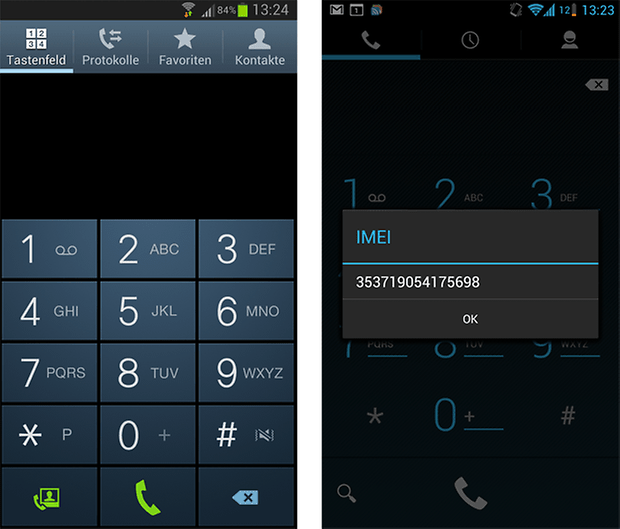
Two Galaxy S3 models after visiting the test site http://www.isk.kth.se/ ~ rbbo / testussd.html. The left model is running the latest Samsung firmware (Android 4.1) while the right is running CM9 (Android 4.0.4) / (c) AndroidPIT
Which phones are affected?
Both the manufacturer and the version of Android is relevent to whether or not the device is at risk. Devices running Android 4.1 Jelly Bean seem not to be affected. However, those devices running Android 4.0.1 and 4.0.3 have been shown to be at risk. Whether the USSD code is accessed via Chrome or Android's native browser also seems to have an effect on the outcome.
These following devices are known to have the security hole:
- Samsung Galaxy S3 running Android 4.0.4
- Samsung Galaxy S2
- Samsung Galaxy Ace, Beam and S Advance
- HTC One W
- HTC One X
- HTC Sensation (XE) running Android 4.0.3
- HTC Desire HD
- HTC Legend
- HTC Desire Z
- Motorola Milestone
- Motorola Atrix 4G
- Motorola Razr running Android 2.3.6
- Huawei Ideos
To find out if your phone is also affected (without putting your phone in actual danger), simply visit this website referred to by Borgaonkar: http://www.isk.kth.se/~rbbo/testussd.html If your phone then immediately displays an IMEI number, then your model runs USSD commands in the background of your phone without prompting you.
How can I protect my phone?
Install a dialing app. If you install an alternative dialer, you should always receive a message which asks you which phone app you want to use to execute the call. You should be careful not to set any dialer as a default, so that the dialog box always appears. This extra step could prevent the USSD code from working.
Additionally, developer and AndroidPIT community member Joerg Voss has also created a small tool which emulates such a dialer and should stop the code from working automatically, so you can protect against such attacks without having to download a full-featured dialer. You can installed NoTelURL directly from the Google Play Store.
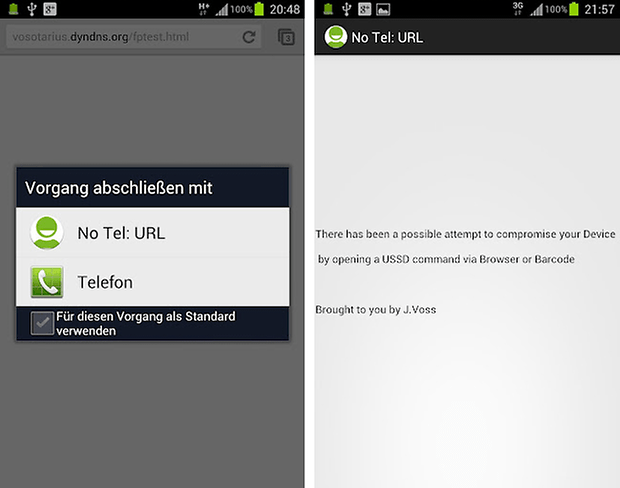
For now, there aren't more elegant solutions. Manufacturers must deliver updates. On that end, Samsung has already announced a patch for those models still affected.
In conclusion, what is the risk to my phone?
The risk is that, upon visiting a website, a USSD code could begin running in the background, which is undoubtedly a serious breach of security. However, you shouldn't panic just yet: so far, no cases in the wild are known where this security breach has been exploited.













Thanks!
Thank you for bringing this very informative article to us. Thank you also for helping us to fix the issue.
Thank you Joerg for a good program quickly. It works great.
I love this community.
Thanks for the tip about the dialers! I already have a custom dialer installed so I'm undefaulting it ASAP!
Dom, thanks, fixed it!
with this in mind, is it not also possible that they could get your phone to dial a premium rate phone number in the background without your knowledge and run up large phone bills?
Hi!
The link to the test page is wrong (have some spaces)
I shorted the test address here: http://bit.ly/P6mKHY
:)
Sony Xperia S with ICS have no problem!!